Deliver Software.
On Time. On Target.
Soar past barriers with UDS, our secure, portable, airgap-native platform, purpose-built for delivering software to military systems.
UDS includes the essential tools to package, deploy, monitor, and sustain mission applications.
Your Open Source Toolkit
UDS CORE
Tech Stack
UDS Core is the foundation of our UDS software delivery platform. It combines the best of open source DevSecOps tools for monitoring, log aggregation, airgap deployment, and more into a secure runtime platform that addresses the unique challenges of deploying and updating software on military systems.

Keycloak
(IDAM)
Prometheus Stack
(Monitoring)
Loki
(Log Aggregation)
Authservice
(Authorization)
Grafana
(Monitoring)
Vector
(Log Aggregation)
Istio
(Service Mesh)
Falco
(Container Security)
Velero
(Backup & Restore)
Metrics Server
(Resource Metrics)
Pepr
(Policy Engine & Operator)
Zarf
(Airgap Deploy & SBOM)
Our Open Source Commitment
We believe that open source software is essential to achieving our vision of global freedom and independence because it provides transparency and eliminates the vendor lock that has plagued military programs for decades. Defense Unicorns is proud of the significant contributions we’ve made to the DevSecOps and Kubernetes communities since our founding, and we are committed to continuing to build and share open source software with the world.
Zarf
Airgap Software Delivery
Zarf is a free, open source tool that enables continuous software delivery of cloud-native applications to systems disconnected from the Internet by securely bundling and delivering all required files and dependencies.

Portable
Package and deploy to airgapped areas.
Consistent
Deploy the same capabilities into highly distributable systems.
Compliant
Access support for SBOM requirements.
Continuous
Stay productive in connected and disconnected environments.
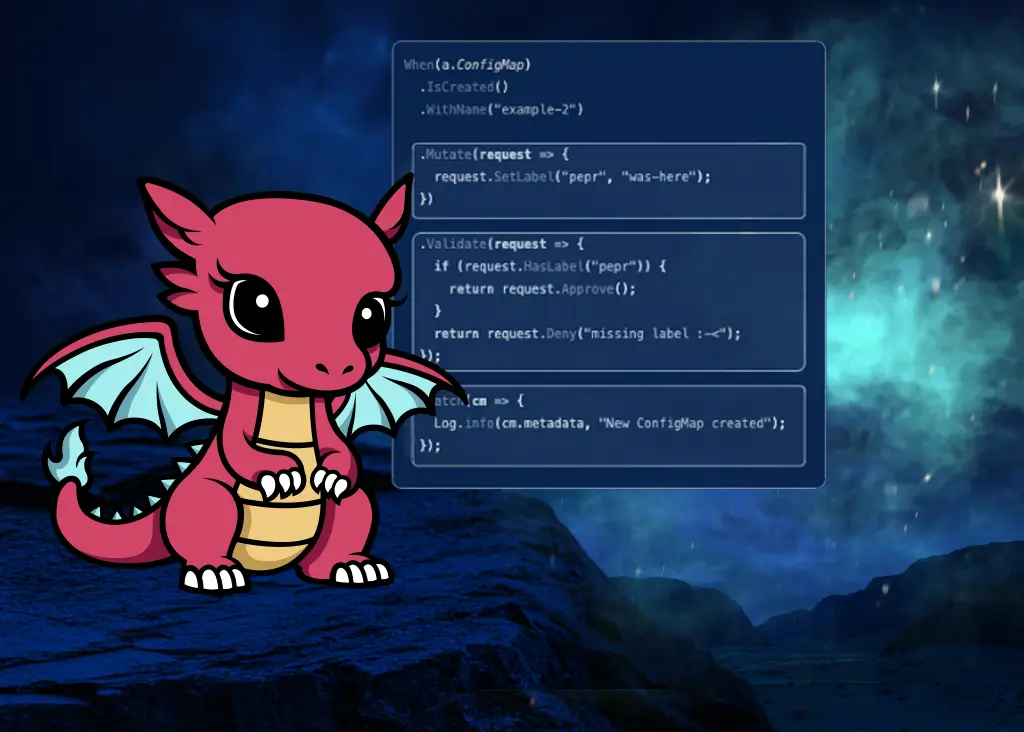
Pepr
Kubernetes Middleware
Made Easy
Pepr is a free, open source tool that helps IT Operations teams of all skill levels manage and modify resources in a Kubernetes (K8s) cluster using easy-to-read, easy-to-write configuration modules.
Create Robust Policy Engines
Codify security policy into corrective Pepr modules that can identify and remediate risk through automatically enforcing K8s best practices.
Seamlessly Connect Applications
Automate the integration of mission capabilities into complex systems with Pepr modules that are reusable across multiple systems.
Automate K8s Scripts
Remove the need for human intervention when issues arise in the cluster or application, by using Pepr modules to remediate the event.
Explore Developer Resources for UDS
Documentation
Dive into the UDS documentation to learn about all of its features.
Tutorials
Learn about using Zarf, Pepr, and UDS with a series of developer tutorials.
Exercises
Get hands-on practice in packaging and deploying applications with UDS.
