
Get Software To Warfighters When And Where They Need It
UDS Registry is Now Available!
Explore UDS RegistryAccelerate Deployments, Slash Costs, & Automate Security
Deploy & Accredit Software 10X Faster
Accelerate deployments and ATO timelines by 50–90% through automated, repeatable workflows powered by UDS Core's open-source foundations.
Enforce Zero-CVE
Strategy at Scale
Automate vulnerability scanning, policy enforcement, and NIST 800-53 alignment, significantly reducing manual security management.
Deploy Anywhere,
Seamlessly
Deliver standardized, vendor-neutral software packages securely to cloud, on-prem, or edge environments, fully supporting airgapped operations.
Boost Efficiency,
Not Headcount
Achieve up to 4x deployment efficiency—reducing operational costs and empowering engineers to focus on innovation, not maintenance.
You Protect Us. We Serve You.










Say Goodbye to Outdated Software

Simple Application Delivery with a Centralized, Self-Service Registry
UDS Registry provides a secure, airgap-ready platform to manage and deploy mission-ready software—without the overhead of maintaining complex infrastructure or integration pipelines. Designed to work seamlessly with Zarf and other UDS tooling, it’s the fast track to delivering trusted applications to any environment.
Pre-vetted packages for secure, repeatable deployments
CI/CD-ready API for DevSecOps workflows
Built-in CVE scanning and access control

Agile, Compliant DoD Cloud Deployments
Simplify deployment and accelerate compliance in multi-cloud and hybrid environments with built-in automation, security enforcement, and real-time observability—purpose-built for government missions.
Continuous ATO workflows with pre-built artifacts
Built-in security compliance (IL5/IL6)
Open-source core with support for licensed integrations
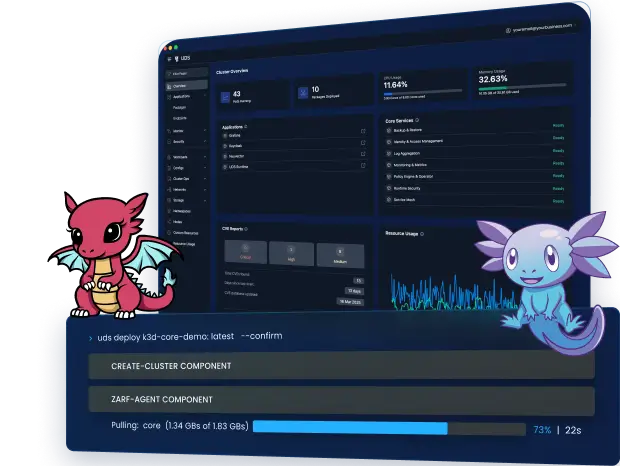
Secure, Reliable Software Delivery-
No Internet Required
Deploy mission-critical software seamlessly into fully disconnected environments—classified or unclassified—using automated and auditable workflows designed for maximum security and resilience.
Consistent, repeatable software deployments
Built-in NIST 800-53 security compliance
Vendor-agnostic, open-core flexibility
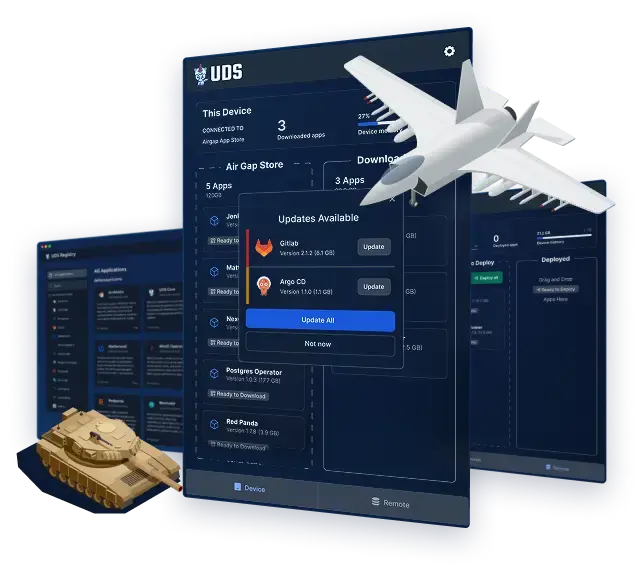
Operate Securely in Offline, Contested & Mission-Critical Environments
Maintain full control of mission software—even in disconnected or contested environments—with secure, instant deployments that keep teams operational at the tactical edge—preserving the digital advantage.
Integrate once, securely deploy to multiple environments
Offline-capable, on-demand updates with UDS Mobile
Pre-integrated, security-vetted software packages from UDS Registry

Mission Impact, Measured.
Utilizing UDS and the CtS (Certificate to Ship) process, the approval time for application upgrades was reduced 90x, from the six-month average to just two days for the Navy.
Using "unicorn" hardened containers a DoD software deployment partner reduced their CVE count by 85% compared to open-source "upstream" equivalents, clearing the path to ATO.
Delivered mission-critical software to the Department of the Navy 4 years ahead of schedule—with NIST 800-53 controls and pre-vetted artifacts accelerating compliance from years to weeks.

Frequently Asked Questions
Defense Unicorns delivers secure, scalable, and vendor-lock-free software deployment solutions for mission-critical environments. We help the DoD, system integrators, and defense teams accelerate software delivery without compromising security or compliance.
We work with DoD agencies, system integrators, and organizations that need to modernize and secure their software delivery. Our solutions are built for national security missions requiring air-gapped, classified, or highly secure environments.
We eliminate delays, automate security compliance, and ensure software runs seamlessly across disconnected, classified, and cloud environments—without vendor lock-in or unpredictable costs.
We integrate security directly into software deployment workflows, reducing the manual compliance burden. Our solutions automate security checks, align with DoD cybersecurity frameworks, and support continuous ATO (cATO) efforts.
✔ Built for Secure, Disconnected Environments - Designed for cloud, on-prem, air-gapped,
and classified networks.
✔ Security & Compliance Integrated - Automates compliance with DoD cybersecurity standards.
✔ Vendor-Lock Free - Open-source and mission-owned, so you stay in control.
✔ Predictable Pricing - Firm-fixed pricing, avoiding cost overruns.
We offer multiple procurement paths, including government contracts and system integrator partnerships.
Talk to our team to discuss your needs, assess your deployment challenges, and explore the best path forward. Whether you need a consultation or a secure deployment plan, we're here to help.


